how we identify ourselves
You probably identify yourself to a computer dozens or even hundreds of times a day. Think of unlocking your phone or laptop; or logging in to Amazon to shop, your company’s intranet to work, and your bank to manage money. Identifying yourself to computers is an everyday activity—but one fraught with peril.
In my observations, many people live in a low-grade state of worry that they are doing something wrong with their digital identity: that they’ll forget their password, that their password is not secure enough, that they’ll type the wrong thing into the wrong field and be locked out of their account.
And they are right to think so. Identity theft and related fraud costs the world economy billions—by some accounts more than all types of physical property theft combined. On the flipside, businesses who build the websites and products that we use in our daily lives bear a huge support cost from dealing with password resets and other account-related confusion.
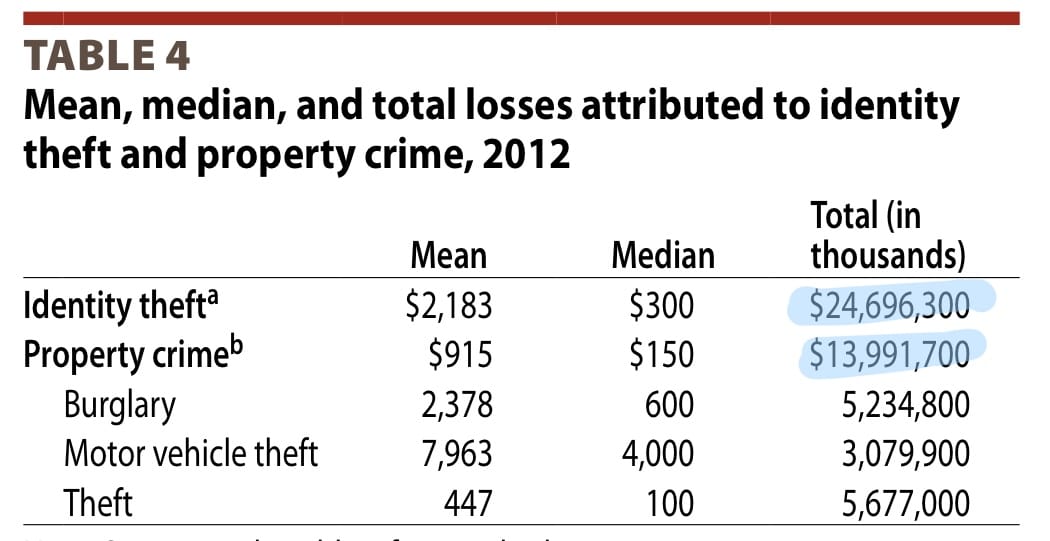
Identity theft ($24B) is more costly than physical crime ($14B).
From Victims of Identity Theft, US Department of Justice (2012)
At a more mundane level, we all face constant friction related to identity. Why can’t Google Docs figure out the correct account to use when accessing a document? Why do I have to use the same password to log into Office 365 that I use to play XBox games? And remind me which sign-in service I used for this website?
It gets worse: physical world activities like banking, real estate, and taxes are shifting online. Physical-world methods of identity typically rely on pseudo-secrets like birthday, mother’s maiden name, social security number, credit card number, or wet-ink signatures. These are laughably easy to find and replicate in the wide world of the internet, and not up to the job of securing our most important transactions.
First, the prior art.
People have been thinking about the identity problem for over a decade, with seminal works like The Laws of Identity and Identity 2.0.
There have been attempts to solve identity with one grand, boil-the-ocean approach such as OpenID, Microsoft Passport, and Mozilla Persona. These failed.
Asymmetric key cryptography (where the user has a private key and only shares the public part) is the clear technological solution, but outside of examples like SSL/HTTPS or ssh’s authorized_keys, it has not found wide deployment. A perfect example of the user experience nightmare that cryptographic solutions foist on users is PGP email.
OAuth and the subsequent profusion of sign-on services is a partial success for certain uses, but I and many others are suspicious of a single company owning your entire online identity.
Who do you trust with total ownership of your online identity?
This is a hard problem. But here are some bright spots in online identity that perhaps we can expand on:
Email is your real online identity. Notion, Slack, and others have seized on this with their magic link logins.
Two-factor authentication via SMS or authenticator mobile apps. While this is often a somewhat clunky user experience, it’s a huge upgrade for security and has become widely deployed. The phone as an identity token is the crucial piece of this puzzle.
Biometric identity (facial recognition, fingerprint readers) is fast, convenient, and “good enough” for personal devices that you control physical access to.
Password managers. This one is tough. On one hand, a password manager is the only responsible way to have an online identity: operating without one is like driving a car without a seatbelt. And yet, they remain out of reach for many people, and therefore not widely deployed, and therefore many websites and apps don’t integrate well with them.
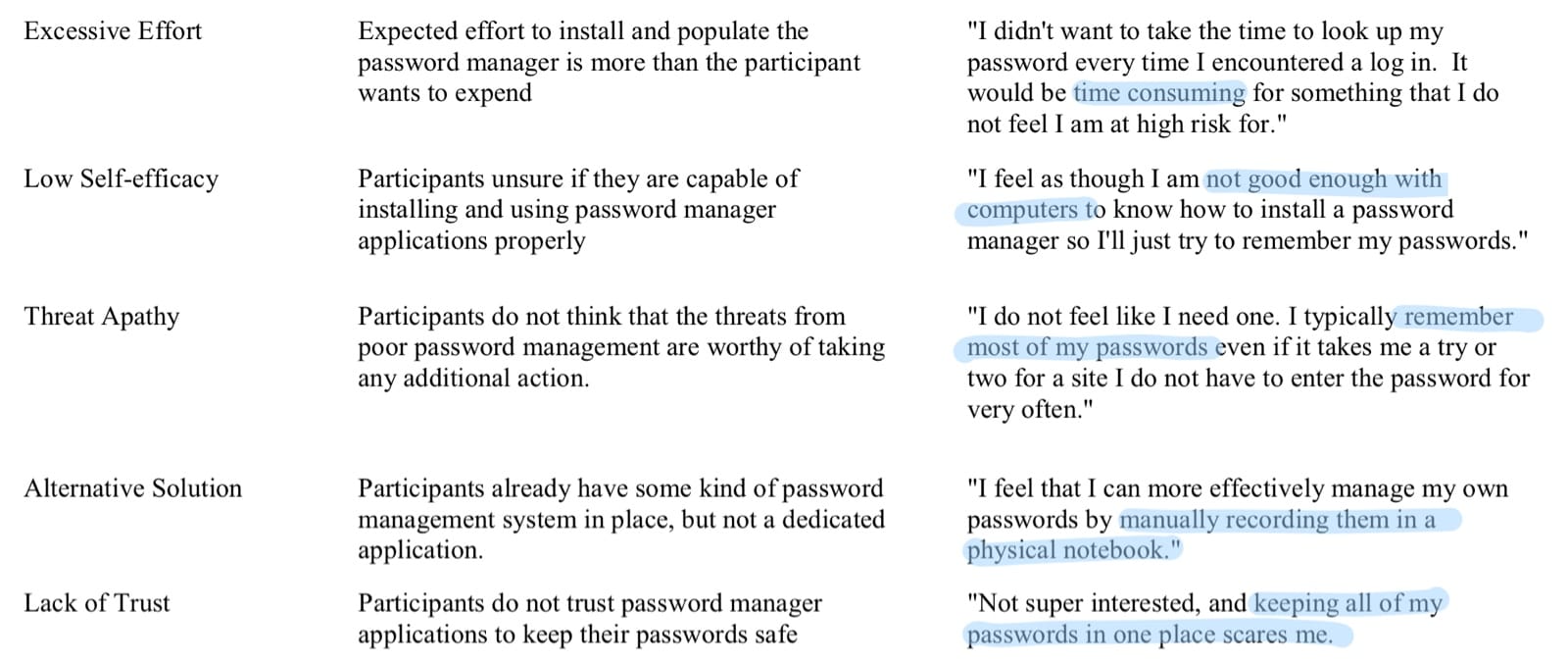
Interview quotes from So Much Promise, So Little Use: What is Stopping Home End-Users from Using Password Manager Applications? (2017)
So the path forward is probably a combination of: embracing the phone as an identity token; public/private key cryptography behind the scenes but insulated from the key management of users; biometrics for physically-accessed devices; email as the uniting identifier; and multi-factor authentication for important transactions dealing with contracts, money, or voting.
The world we have: A disastrous hodge-podge of physical-world identity (social security numbers and birthdays), confusing and guilt-ridden digital identity (passwords, password managers, security questions), and identities owned by companies instead of individuals.
The world I want: Digital identity that is easy to use, private, and secure.